The Snappt Fraud Forensics team is our investment in ensuring that we are always on the cutting edge of fraud detection. This team identifies and researches potential vulnerabilities, extracting the learnings to update and improve our system.
While no system will ever be 100% accurate, this process has helped us to stay multiple steps ahead of prospective fraudsters and earned us our industry-leading 99.8% accuracy rate.
Why does Fraud Forensics matter?
When Snappt created the first-ever document fraud detection technology, we were in uncharted territory – after all, this wasn’t something that had ever been done before. As a result, we turned to the best practices of other industries so that we wouldn’t have to create all our strategies and policies from scratch.
Our team has a deep background in cybersecurity and has believed from the outset that there are several similarities between cybersecurity and fraud detection. One of the most obvious parallels is that in both industries, there is an arms race between the good and bad actors in the space.
Cybersecurity companies like Symantec have vast teams dedicated to researching and tracking vulnerabilities, and so from day one, we set out to mirror this process. As our company has grown, we have heavily invested in our fraud forensics team because we know that the race is just getting started. If we don’t continue to innovate, we will eventually become obsolete.
How does our team help keep you safe?
Our high-level process has four steps: Identify new vulnerabilities, Analyze those vulnerabilities, Extract new learnings or information, and then iterate on our core engine.
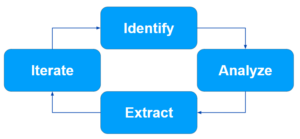
Identify new vulnerabilities
Finding new data on fraud might sound challenging, but we live in an era when fraudsters openly discuss their crimes in public. Some of our best sources for finding and tracking fraudsters include:
- Tik Tok
Even a simple Google search for “fake paystubs” will result in thousands of results like this:
Ultimately, it isn’t much of a challenge to find these fraudsters, as they hide behind First Amendment laws (they claim to be educational resources only). The net result is open discussion online regarding clearly illegal activity. While this is bad for the industry overall, the silver lining is that it makes it incredibly easy for our team to find and track fraudsters.
Analyze vulnerabilities
The first thing we do when identifying a new vulnerability is check it against our vast database of known vulnerabilities (similar to a database of known viruses). One of our earliest learnings was that fraudsters seemed to be perfectly comfortable stealing from or copying each other. For example, we identified six unique vulnerability patterns across over 300 sources of online pay stubs, indicating that they likely originated from only a handful of sources.
Next, we test the documents against our system to determine if the vulnerability is currently open or active. Given the propensity for fraudsters to copy each other, our most common result is that the identified vulnerability has already been addressed and closed.
An example is ExifTool, a vulnerability that has been known and closed for years, but is still discussed openly online as a way to “beat” fraud detection.
The tool works by wiping visible document metadata, leaving you with the equivalent of a person with no fingerprints. This is an easy action to detect, and thus, it is a simple edit flag for our system.
Even though this technique would not work on a modern fraud detection system, fraudsters still refer to it as though it does, and a large number of fraudsters offering “money-back guarantees” rely on this outdated fraud technique.
Extract learnings
When a new fraud technique or source is discovered, our team responds rapidly by extracting all information from this new vulnerability.
The advantage of running millions of documents through our system is that it makes it incredibly easy to find and react to these threats. Our team typically completes the extraction process within one to two business days, resulting in a very small window during which a vulnerability remains active.
Iterate on the core engine
With the extracted vulnerability information in hand, our Fraud Forensics team passes these learnings on to our R&D and Engineering teams, who quickly incorporate these new insights into our process to update our core detection engine.
This is again an area that is significantly aided by our company’s size (and the number of documents we’ve scanned) – what would take a smaller company days or even weeks to adjust to can be solved by our team in minutes.
Current vulnerability landscape
In the early days, our fraud forensics team was constantly identifying and closing new vulnerabilities, as this was brand-new technology. As the years have passed, our system has undergone rapid improvements to address the known fraud vulnerability landscape, resulting in a significant reduction in active vulnerabilities.
Although it is incredibly uncommon for us to find an active vulnerability, it does still happen – this year, we have only one recorded instance of an active vulnerability, which was identified and closed within two business days.
Just like antivirus software, we will always face zero-day attacks (new vulnerabilities that the industry discovers and reacts to). Our heavy investment in our fraud forensics team ensures that we can stay ahead of any changes to known fraud techniques and keep you one step ahead at all times.

Chat with our sales team to learn about our comprehensive fraud solution

